
Heading 1
Webroot™
Business Endpoint Protection
Advanced machine learning and cloud-based protection
-
Multi-vector protection against malicious files, scripts, exploits and URLs
-
Remote policy definition and management
-
Precision monitoring and roll-back capabilities for auto-restoring and infected files

What is Endpoint
Protection?
Endpoint protection, or endpoint security, is a general term that describes cybersecurity services for network endpoints, like laptops, desktops, smartphones, tablets, servers and virtual environments. These services may include antivirus, antimalware, web filtering and more.
Endpoint protection helps businesses keep critical systems, intellectual property, customer data, employees and guests safe from ransomware, phishing, malware, zero-day threats and other cyberattacks.
Why is Endpoint Protection important?
Businesses of all sizes are under constant attack. With the volume and velocity of attacks, it’s never been more critical to stop malware, ransomware, phishing and other damaging attacks aimed at your users and systems.
Webroot Endpoint Protection solves these problems by delivering an award-winning management console with comprehensive protection that complements an organization’s cyber resilience strategy. Webroot harnesses the power of cloud computing and real-time machine learning to continuously monitor and adapt endpoint defenses.
Without protection, companies risk losing their critical data, paying significant ransoms and losing the ability to conduct business. Many companies are also subject to privacy and compliance regulations, so there is additional risk of further financial loss and damage to their reputation in the case of a security breach.

Benefits
Purpose-built for MSPs and SMBs
Hassle free deployment and fully operational in 30 seconds
Superior efficacy against zero-day threats
features
Collective threat intelligence
-
Powered by advanced machine learning
-
Predictive analytics provides automated protection against zero-day threats
-
Requires minimal human interaction
Superior speed and efficiency
-
Nimble agent designed for minimal footprint and system performance impact
-
Easy to deploy and installs in seconds
-
Ultra-fast scans
Cloud-based architecture
-
Continuously correlates and analyzes data from 95+ million sensors
-
Access to advanced computing power
Nationwide Healthcare Services Rests Easier with Webroot Endpoint Protection
Nationwide Healthcare Services switched to Webroot Endpoint Protection for its ease-of-use, time savings, and low system resource usage Webroot Endpoint Protection met their qualifications for cybersecurity liability insurance.
WEBROOT®
Business Mobile Security
MOBILE SECURITY FOR SHOPPING, BANKING, AND BROWSING

Why Mobile Security?
Threats from mobile malware on Android™ devices continue to grow exponentially. Each year, Webroot categorizes millions of new apps as suspicious or malicious. And iOS attacks are on the rise, too. With more and more shopping, banking, and browsing happening on mobile devices, hackers are devoting greater effort to compromising these devices. Protecting them is more important than ever.
How Webroot Can Keep You Safe
Secure mobile web browsing identifies malicious websites and protects against phishing and other social engineering tactics aimed at seizing your personal data in real time. Android antivirus automatically protects, scans, and checks all applications and updates for threats without interruptions. In addition to cyberattacks, mobile devices are highly vulnerable to theft and loss due to their size and portability. Webroot allows you to lock, scream, or wipe Android™ devices once they've been lost or stolen.
WEBROOT®
DNS PROTECTION
Secure your DNS connection against cyberattacks, get total visibility into web usage, and enforce acceptable web usage policies to reduce security risk.

What is DNS protection?
Before we talk about DNS security, you need to understand the DNS. The domain name system (DNS) works like a phone book for the internet. When a user enters text into a browser, DNS servers take that input and translate it into the unique internet protocol (IP) addresses that let the browser open the desired site. But DNS protocols were never designed with security in mind, and are highly vulnerable to cyberattacks, such as cache poisoning, DDoS, DNS hijacking, botnets, C&C, man-in-the-middle, and more.
By redirecting users’ web traffic through a cloud-based, DNS security solution, businesses and MSPs can finely tune and enforce web access policies, ensure regulatory compliance, and stop 88% of threats at the network’s edge—before they ever hit the network or endpoints.
Webroot® DNS
Protection can stop
88%
of threats at the network's edge
WEBROOT®
SECURITY AWARENESS TRAINING
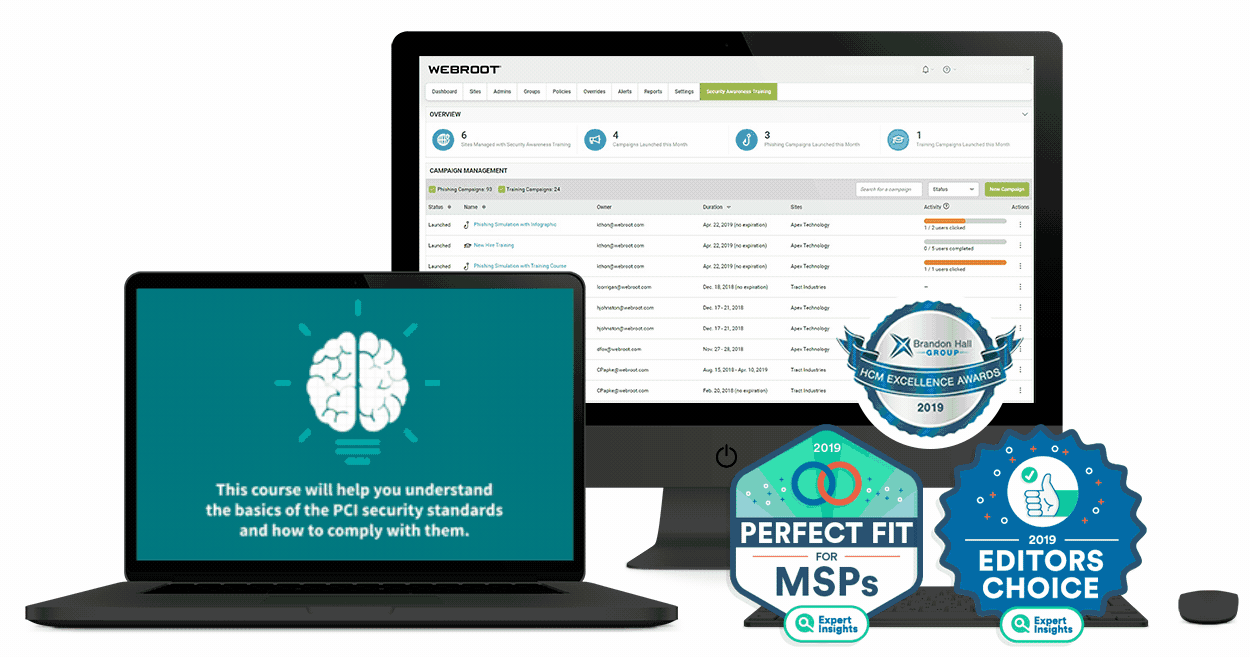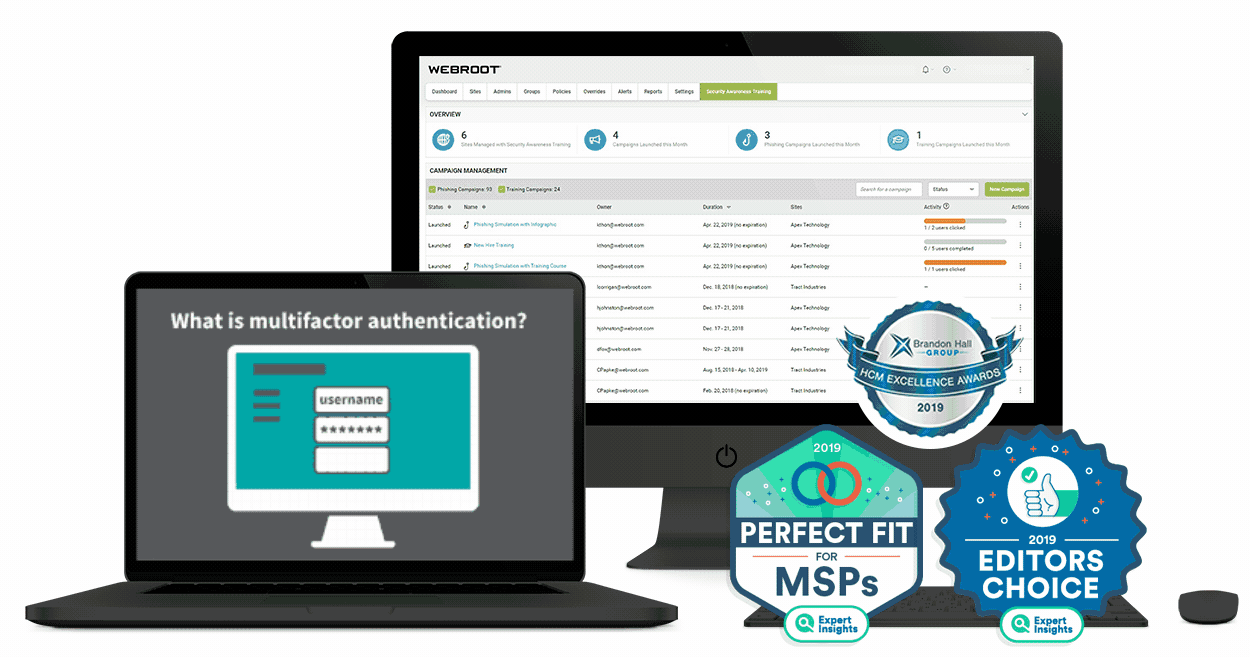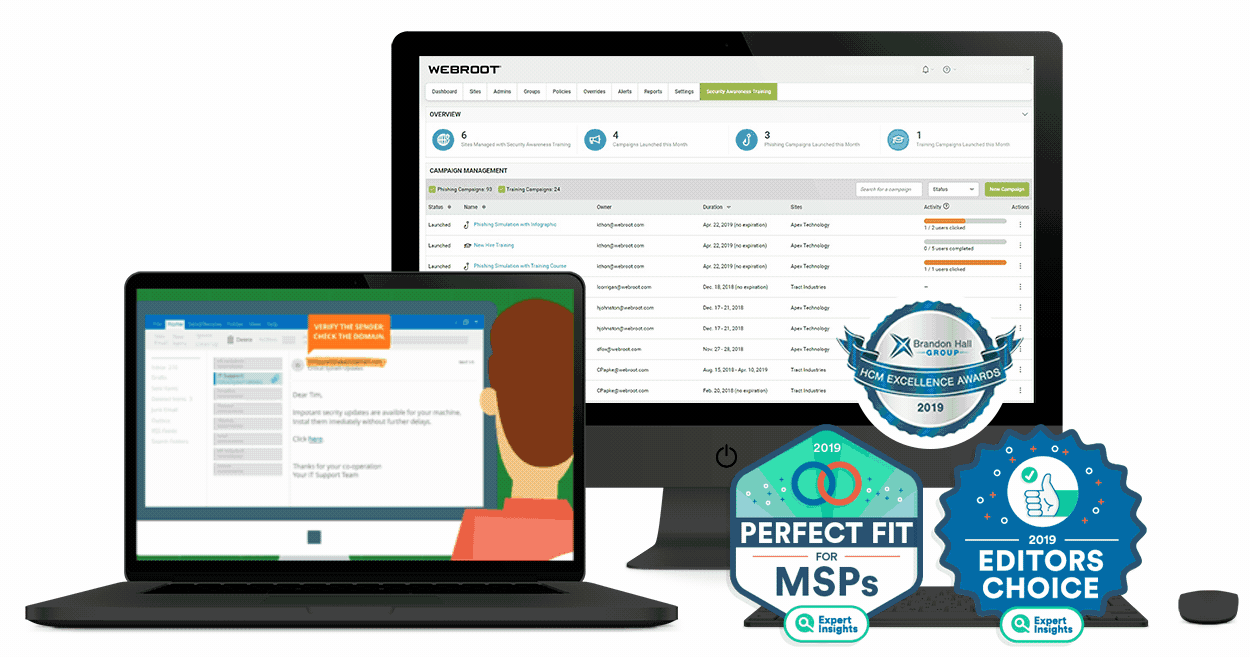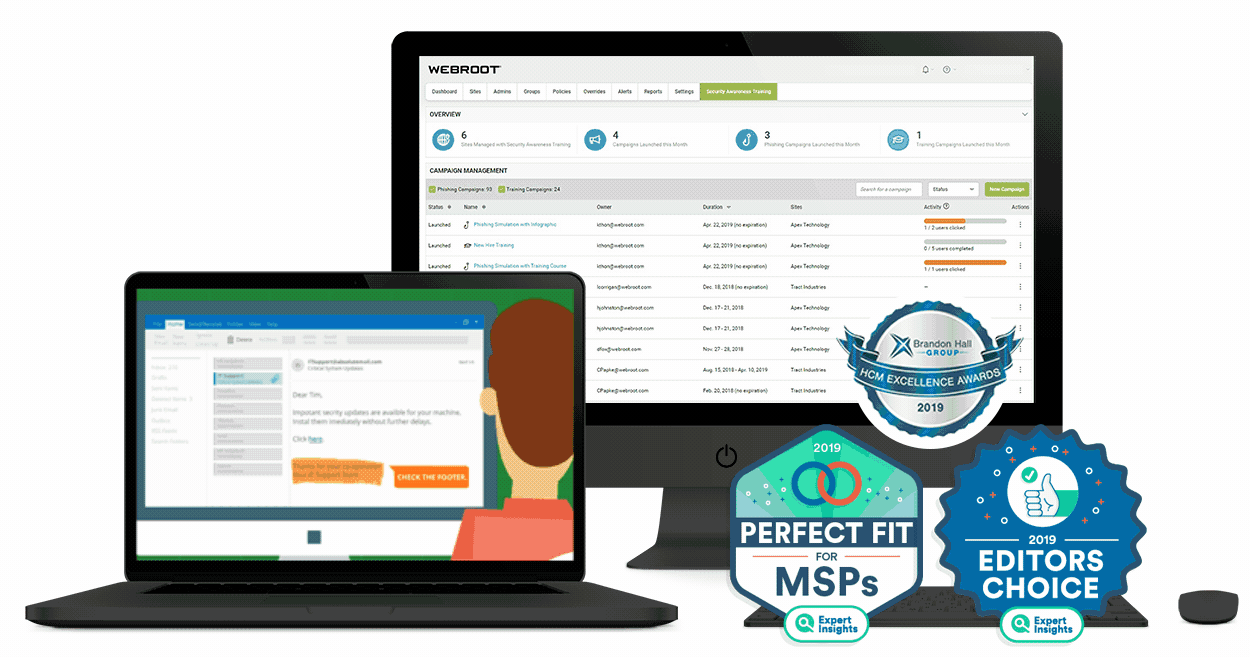
What is security awareness training?
Security awareness training is an education process that teaches employees about cybersecurity, IT best practices, and even regulatory compliance. A comprehensive security awareness program for employees should train them on a variety of IT, security, and other business-related topics.
These may include how to avoid phishing and other types of social engineering cyberattacks, spot potential malware behaviors, report possible security threats, follow company IT policies and best practices, and adhere to any applicable data privacy and compliance regulations (GDPR, PCI DSS, HIPAA, etc.)
90%
of successful network breaches
were caused by user error*
*2017 Verizon Data Breach Report
.png)